IT/OT Convergence: The Opportunities and Risks of Networked Production
IT and OT are merging in networked production. This brings opportunities for efficiency, as well as insights. But security risks caused by attacks on OT systems demand new strategies.
Cybersecurity in Production: Networked OT Requires IT Security Standards
As production becomes more networked, IT and OT are growing closer together. This merging of operative technology (OT) on the shop floor and IT systems designed for production planning and corporate management means greater efficiency, flexible control, and better insights into production metrics. But at the same time, the Industrial Internet of Things (IIoT) increases operative complexity. Furthermore, networked OT is becoming increasingly vulnerable to security risks that were previously known only in IT. As a consequence, attacks on OT systems are becoming more frequent and more professional, and OT can become a weak point in overall systems and threaten entire networks. That’s why defending against cyberattacks and preventing technically induced outages demands new strategies and new expertise in production.
Unclear Division of Responsibilities Between IT and OT
In practice, IT and OT are still operated by separate departments with different briefs. This can cause unclear responsibilities and conflicting goals. It’s often difficult to determine who is responsible for maintaining, updating, and monitoring these shared systems. This can cause conflicts and incomplete processes, especially when systems fail, or security incidents occur.
Standardization plays a key role in establishing clear responsibilities in IT/OT convergence and minimizing conflicting goals. Learn more in our video (2 min., 25 sec.) with Oliver Müller, Senior Manager at BOSCH.
OT Data Management & Resilience Check
Well positioned? Uncover optimization potentials in your production data management in just 3 minutes.
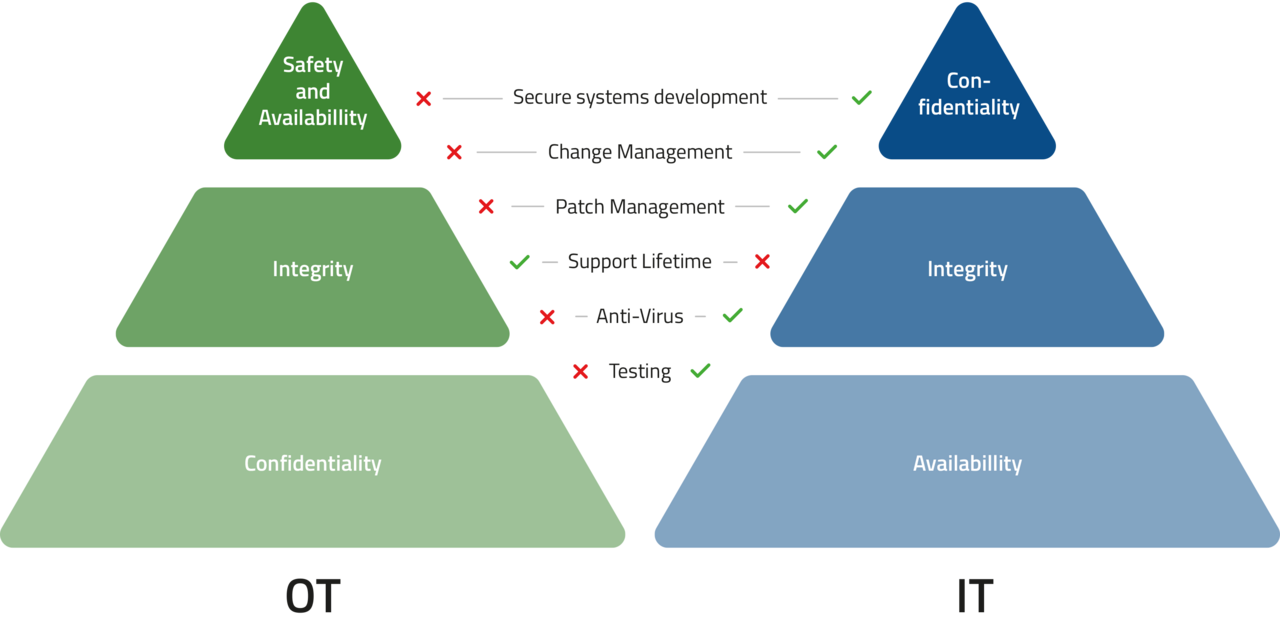
The Potential for Conflict Between IT and OT
The convergence of IT and OT is producing clear points of conflict that can manifest in different ways. Diverging demands on network infrastructure, industrial security, and data management only serve to amplify these conflicts.
Network infrastructure
- IT focuses on flexible, scalable, standardized network infrastructure.
- OT primarily requires stable, deterministic network infrastructure to enable continuous operation and the real-time control of production facilities.
Industrial security
- IT prioritizes protection against external threats such as cyberattacks, viruses, and malware.
- OT aims to ensure the safety and security of production environments so as to prevent business interruptions, hazards to employees, and damage to equipment.
Data management
- IT focuses on centralized data storage, data analysis, and maximum accessibility for company-wide applications and decision-making processes.
- OT focuses primarily on capturing, processing, and storing large quantities of data from production facilities in real time. This allows processes to be monitored, systems to be controlled, and productivity to be optimized.
Ensuring Compliance: Regulations Affecting IT and OT
Manufacturing companies are subject to numerous regulations and standards. Soon we will have NIS-2, yet another set of regulations governing information security. Businesses will have to ensure that all their systems comply with these regulations. Here are some important examples of international laws and guidelines that relate to IT (information technology) and OT (operational technology):
ISO 27001
This is an internationally recognized standard for information security management systems (ISMS). The standard can be applied to both IT and OT environments, with the aim of establishing complete security management systems.
IEC 62443
This series of standards addresses cybersecurity in industrial automation systems. It defines requirements and recommendations on how to securely develop, implement, and operate OT systems. This means it relates to IT as well as OT aspects.
You hear people running around saying all plants will have SIO and all the PLCs will be in the cloud. I don't think that’s going to. I think plants are more than likely going to adopt the zero-trust framework which a lot of OT and IT people are talking about these days and try to put all their control in the cloud.
OT as a Point of Attack
Networking in production requires that all of the systems involved comply with a recommended set of cybersecurity standards. In practice, many OT systems are outdated, which means they’re not designed to support the integration of modern IT systems. Potential vulnerabilities can become doorways into entire automation networks. That’s why IT tends to consider OT a major source of potential vulnerabilities. Other potential reasons:
Lack of segmentation
OT networks are often inadequately shielded. This means that critical systems and control devices may be connected to other networks or the internet. That in turn increases the risk of unauthorized access and malware infection.
Insufficient authentication and access control
Most OT environments have always been autonomous and employ weak or insecure authentication and access control mechanisms, despite increasing networking. This can facilitate unauthorized access to control devices and allow the manipulation and interruption of industrial processes.
Insecure remote access and inadequate overall monitoring
Insecure remote access in OT opens up opportunities for attack. Highly networked environments are often inadequately secured, and remote access can endanger not only OT but also central corporate systems. A lack of overall monitoring in OT systems permits undetected security incidents and attacks and hinders effective countermeasures.
OT Data Management & Resilience Check
Well positioned? Uncover optimization potentials in your production data management in just 3 minutes.